From webinar to action: expert insights to safeguard your ad dollars
Your mobile game’s UA dashboard lights up with exciting metrics. A new campaign is delivering app installs at an impressive $2.50 CPA—half the cost of your established networks. The attributed users seem immediately engaged with your game, triggering in-app purchases within hours of downloading. You and your colleagues are thrilled. Some time later, you discover that 94% of these “users” came from jailbroken devices, the purchases were scripted events that never cleared actual payment processors, and your shiny new traffic partner systematically deployed automated install farms to defraud dozens of advertisers. What looked like marketing gold was actually fool’s pyrite—and you were certainly not alone in falling for the deception.

The $100+ Billion Problem
The digital advertising ecosystem harbors a $100+ billion problem that most marketers would prefer not to think about. Left unchecked, mobile advertising fraud—now the second-largest organized criminal enterprise on the planet—quietly siphons upwards of 40% of advertising budgets. Unlike other forms of marketing waste, fraud actively disguises itself as legitimate performance, creating compelling dashboards that mask devastating losses.
What makes mobile ad fraud particularly insidious is its sophistication. Gone are the days of crude bot farms and obvious click flooding. Today’s fraudsters deploy intelligent algorithms that attune to device activity, simulate realistic user journeys, and exploit attribution windows with surgical precision. They understand your measurement infrastructure better than many of your marketing colleagues do, crafting schemes that satisfy every technical requirement.
The stakes extend beyond immediate budget impact. Plain and simple, ad fraud is serious criminal activity. On top of that, fraudulent traffic skews optimization algorithms, corrupts audience insights, and undermines strategic decision-making across marketing operations. When fraud masquerades as high-performing inventory, it bleeds budgets and may mislead teams into doubling down on fundamentally worthless traffic sources.
Expert Intelligence: Key Insights from Kochava’s Fraud Detection Webinar
Kochava recently hosted a technical deep-dive webinar to cut through fraud’s elaborate disguises, spotlighting detection methodologies refined through hundreds of investigations. Led by Grant Simmons, VP of Kochava Foundry, and Tyler Levasseur, Manager of Foundry Data Analytics, the session unpacked how statistical analysis can expose even the most cleverly crafted fraud schemes.
The duo walked through real-world detection cases, from basic click injection to advanced “smart click flooding” that selectively targets iOS devices using cellular IP addresses for more efficient attribution gaming. Their collective experience and success leverages a key reality: While individual fraudulent events may appear legitimate, fraudsters struggle to randomize every variable simultaneously. This inherent limitation creates statistical patterns that reveal themselves at scale—a foundation of effective fraud detection.
”Fraudsters have a hard time manufacturing everything that needs to get randomized.
Grant SimmonsVP, Kochava Foundry
For example, Levasseur demonstrated how falsified transparency shows up in data, including cases where thousands of different site IDs move in exact unison—a clear indicator of manufactured traffic “randomization” rather than genuine inventory diversity. His explanation of time-to-install (TTI) anomalies showed how fraudsters attempt to avoid detection by spacing out install timing, creating unnatural distribution patterns that expose scripted behavior.
The session emphasized that effective fraud mitigation requires both detection and customization. As Simmons notes, “We want to build you a chainmail suit here, and we can build one custom for you.” This involves configuring verification rules around specific geos, device types, and timing parameters tailored to each advertiser’s platforms and traffic patterns.
Your Pressing Questions Answered
Following the webinar, the Foundry Team gathered questions from attendees seeking to apply these principles to specific challenges. Read on for detailed answers provided by Simmons to help marketers identify, investigate, and mitigate fraud across their campaigns.
Suspect fraud in your campaigns? Request an Ad Fraud Audit to uncover any nefarious patterns.
Foundation & Assessment
What range of fraud percentages from data sources is considered “acceptable” in digital advertising?
Without rigorous preventative measures, upwards of 40% of ad budgets may be lost to fraud. This estimate, drawn from industry analysis and Kochava’s extensive fraud investigation experience, represents the potential impact when advertisers operate without capable detection systems.
While advertisers are generally resigned to accepting moderate levels of fraud (single- to low double-digit percentages), the aspiration should always be to minimize this to the lowest feasible rate through vigilant detection and mitigation systems rather than writing off a set percentage as “normal.” The goal is to create an environment where fraud becomes economically unviable for bad actors.
What simple metrics can CMOs use to quickly estimate their ad fraud losses and actionable next steps?
CMOs should monitor click flooding indicators, install validation failure rates, percentage of jailbroken or rooted devices receiving attribution from specific publishers, and time-to-install (TTI) distributions. These metrics serve as early warning systems that don’t require deep technical expertise to interpret.
Unusually high concentrations of jailbroken devices (anything approaching double digits from a single source), disproportionate TTI clustering (installs occurring within seconds of clicks), and high authentication failure rates signal fraud risks. For perspective, Kochava’s install authentication disqualifies about 1.8% of all install traffic, but some individual networks show install authentication failure rates as high as 40%—a clear red flag warranting immediate investigation.
Establishing verification rules and regularly reviewing violation reports are recommended first steps for rapid detection and action.
What CTR levels should be treated as suspicious?
Click-through-rate (CTR) values above 10% warrant investigation. In legitimate advertising environments, CTRs rarely exceed single digits consistently, as genuine user engagement follows predictable patterns based on creative quality, audience targeting, and placement context.
CTRs above 100% represent a mathematical impossibility in legitimate advertising—indicating either gross errors in measurement or deliberate manipulation wherein impressions are underreported and/or clicks are fraudulently manufactured without legitimate ad views. Always investigate campaigns with abnormally high CTR for data integrity issues, as they often reveal broader fraud schemes affecting multiple metrics.
Detection Fundamentals
How can fraudulent conversions like app installs be reliably detected?
Several techniques help expose fraudulent installs, ranging from technical verification to behavioral pattern analysis:
- SDK-based device authentication: Validates installs against expected device signatures and behaviors
- Install referrer analysis: Confirms that traffic origins match claimed sources available via Google’s Install Referrer API
- TTI distribution analysis: Unnatural clustering of installs immediately post-click signals automation rather than human behavior
- Rooted/jailbroken device tracking: Unusual spikes indicate possible fraud rings operating modified devices
- Organic pattern comparison: Genuine user patterns differ substantially from manufactured ones in timing, geography, and post-install behavior
In the webinar, we highlighted how fraudsters often leave digital fingerprints in error logs. Looking for nonsensical device IDs, error messages like “query exception, unable to open login,” or SQL error strings can surface scripted bot activity that fails during execution.
What outputs do traffic verification tools provide?
Robust traffic verification tools produce comprehensive audit trails, enabling both immediate action and long-term optimization:
- Detailed reports showing which ad signals fail verification and specific reasons (e.g., timing anomalies, blocklisted entities, device authentication issues)
- Ongoing partner-level summaries showing accepted and rejected traffic with trend analysis
- Actionable datasets and exception logs for informing network partners and enabling dispute processes or contract renegotiations
While not always directly exportable as platform-ready audience segments, these outputs empower advertisers to block fraudulent traffic sources, optimize spend allocation, and define custom segments for further targeting or exclusion. The key is treating verification as an ongoing audit function rather than a one-time check.
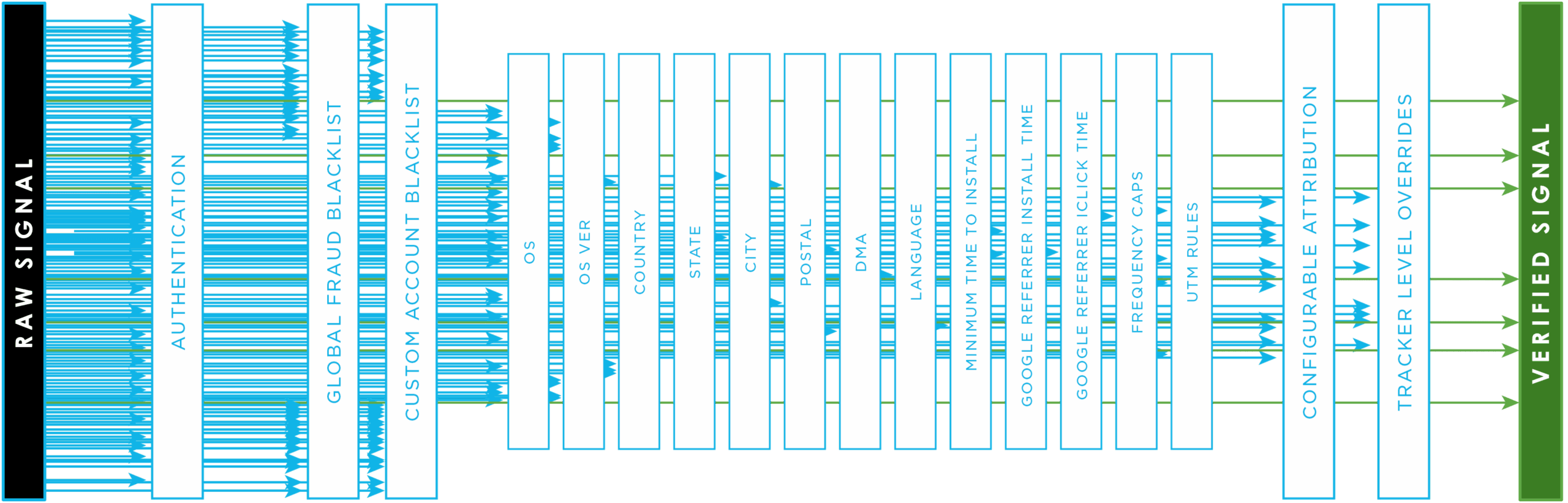
Kochava Traffic Verifier uses a multi-layered detection protocol to identify and mitigate waste in real-time.
Which tools detect and alert on ecommerce session hijacking?
Session hijacking—where fraudsters intercept legitimate user sessions to claim attribution for organic conversions—requires specialized detection beyond standard fraud monitoring. Best practices involve deploying web application firewalls (WAFs), monitoring session token integrity, employing device fingerprinting, and using behavioral anomaly detection to identify suspicious session patterns in real-time.
Advanced solutions can detect when session characteristics suddenly change mid-journey (different IP addresses, device signatures, or behavioral patterns), indicating potential hijacking attempts. The goal is to maintain session continuity verification throughout the conversion funnel.
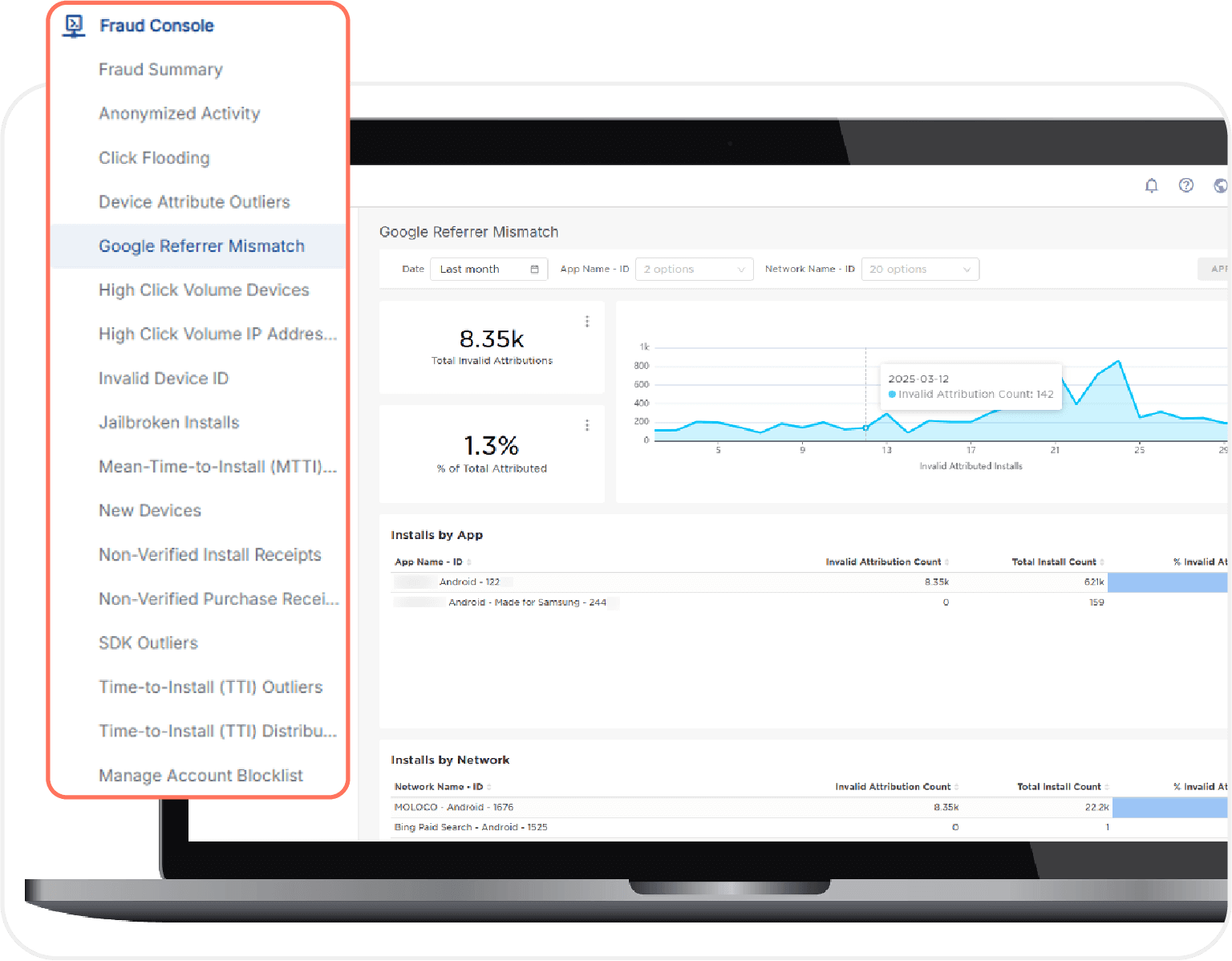
Within the redesigned Kochava platform, the Kochava Fraud Console has been overhauled and expanded to include additional fraud monitoring dashboards, including a brand new Blocked Traffic Summary dashboard. Check out this blog post for more information.
Marketers leveraging Kochava as their mobile measurement partner (MMP) are encouraged to activate the full strength of Kochava’s anti-fraud capabilities.
Fraud Types & Tactics
What fraud types are prevalent in retargeting campaigns, and how can they be identified?
In retargeting, click flooding dominates the fraud landscape—fraudsters generate massive volumes of false ad signals concentrated across very few devices to maximize attribution claims from existing users. This differs from user acquisition fraud, which focuses on manufacturing new attributed users.
Analyze device-level distribution of ad events: If single devices account for abnormally high click volumes (sometimes tens of thousands), this is an immediate red flag. In the webinar, we noted cases where individual devices showed 30,000+ attributed clicks across apps & campaigns—physically impossible for human interaction.
Other retargeting fraud tactics include recording impressions as clicks to boost attribution priority. Cases where clicks outnumber impressions or CTRs exceed 100% indicate systematic manipulation. Monitor suspicious referral strings, OS type distributions, and cohort anomalies to enhance detection capabilities.
How do fraud strategies differ between retargeting and user acquisition campaigns?
The fundamental distinction lies in optimization goals: Retargeting fraud maximizes events per device rather than new installs, while UA fraud focuses on maximizing unique attributed install conversions.
Retargeting fraud favors click flooding and recycling ad events for known devices, exploiting the fact that these users already exist in attribution systems. Fraudsters can generate thousands of false clicks knowing that eventual organic app usage will trigger attribution to their inflated click volumes.
User acquisition fraud exploits install farms and click injection designed to manufacture entirely new attributed users through device emulation, app store manipulation, or hijacking genuine download processes. These schemes require more sophisticated infrastructure but offer higher per-conversion payouts.
What are the newest deep-funnel fraud tactics?
Modern fraudsters can script comprehensive post-install event sequences to mimic legitimate user funnel progression, including fake in-app purchases, registrations, and payment events that at times even clear through actual banking systems. We have come a long way from simple install fraud toward complete user journey simulation.
However, telltale signs emerge when analyzing conversion quality. Look for dramatic drop-offs in completion rates at specific funnel stages when comparing paid vs. organic cohorts, or mismatches between reported event completion and actual business outcomes (e.g., revenue recognition, customer service interactions).
Advanced fraud operations may trigger legitimate payment events while ensuring that the underlying user accounts remain dormant, creating impressive and inherently impossible conversion metrics. Scrutinizing event sequences and implementing receipt verification (comparing in-app purchases against store receipts) can reveal these cunning schemes.
Are there algorithms to identify MFA (made-for-advertiser) traffic?
Made-for-advertiser sites represent a gray area between fraud and low-quality inventory, but detection follows similar principles to fraud identification. MFA identification involves analyzing site/content quality metrics, ad-to-content ratios, and engagement pattern comparisons across traffic sources.
Deploy blocklists of known MFA sites coupled with behavioral metrics such as bounce rate, session duration, and page views per session. If there’s a cohort of suspected incentivized installs, examine post-install behavior patterns: Do users all behave identically—completing exactly one level and then abandoning the app, or viewing a specific store item and nothing else?
During the webinar, we emphasized looking for unnatural uniformity in user behavior, as legitimate users exhibit natural variation in engagement patterns that MFA and incentivized traffic often fail to replicate convincingly.
Advanced & Platform-Specific Challenges
What’s your experience auditing Google products like PMAX, Discovery, and PPC mobile traffic for fraud?
In the webinar, we expressed particular skepticism about “networks grading their own homework,” with PMAX and PPC requiring especially careful independent monitoring. Large platforms like Google possess sophisticated fraud detection, but they also have incentive to maximize advertiser spend.
We recommend vigilance around potential zombie conversions—attributed events that satisfy technical requirements but lack genuine user intent or business value. Focus on measuring post-install/event quality rather than relying solely on claimed conversions for campaign evaluation.
All major buying platforms—including Google’s—can be susceptible to fraud without careful, independent monitoring of downstream quality events. The key lies in implementing parallel measurement systems that verify platform-reported performance against actual business outcomes and user behavior patterns.
How should marketers investigate anomalies such as dozens of apps generating clicks from US cities, with one app showing 100% clicks from a single city, VPN usage, and 60%+ CTR?
This scenario exhibits multiple fraud indicators that warrant immediate investigation. The combination of geographic concentration, technical anomalies, and impossible performance metrics suggests coordinated fraud infrastructure rather than isolated issues. Your analysis has already identified key warning signs: geographic concentration anomalies, VPN usage patterns, and statistically impossible CTRs.
Expand the investigation by examining:
- Timing patterns: Do clicks cluster around specific times or follow unnatural regular intervals?
- OS and referral string analysis: Are device signatures consistent with claimed traffic sources?
- Post-install activity assessment: Compare conversion rates and engagement patterns for these suspicious cohorts against baseline performance.
- TTI and installation funnel behaviors: Look for artificial patterns in user journey timing.
These steps can reveal manufactured installs, fraudulent click traffic, or systematic attempts to game attribution at scale.
Check out the full webinar on demand—including real-life case studies—as well as our array of fraud prevention offerings.
The Path Forward: Building Your Fraud Defense
Given the severity ($100 billion+) of the matter, your measurement partner must be able to leverage robust mobile ad fraud detection and mitigation techniques. Our webinar experts emphasized that effective fraud prevention requires treating detection as an ongoing process rather than an occasional audit. As fraudsters adapt their approach, successful marketers must rigorously refine verification rules, analyze new traffic patterns, and maintain vigilant oversight of campaign performance.
Simmons notes an optimistic perspective on the role of artificial intelligence in fraud detection, suggesting that while AI may accelerate the “cat and mouse game” between fraudsters and defenders, it also offers unprecedented opportunities for defense. With access to petabytes of historical campaign data, AI-powered detection systems could identify anomalous patterns at scales impossible through manual analysis.
The encouraging news is that the fundamental limitation faced by fraudsters remains unchanged: Despite advancing technical might, they still struggle to randomize every variable simultaneously. This creates statistical fingerprints that become visible through proper analysis—giving determined marketers the upper hand in protecting their advertising investments.
Ready to audit your campaigns for fraud risks right now? Kochava Foundry has conducted hundreds of fraud investigations, helping brands recover millions in misallocated ad spend. Request a fraud consultation to discover what patterns might be hiding in your campaign data—and what steps can immediately improve the quality of your traffic.



