iOS 17, Privacy Manifests, SKAN 5, and new Vision Pro for AR
There has been no shortage of predictions on what Apple would announce at this year’s Worldwide Developer Conference (WWDC) 2023. With over a million users live streaming the day-one keynote on YouTube, Apple delivered more than a few surprises. Reactions have been mixed to the new Vision Pro headset for augmented reality (AR), but I sure wouldn’t mind getting one for my next birthday.

TLDR: Here are 5 key takeaways in a minute or less:
- New Privacy Manifests appear to be the next step in Apple’s march against the collection and usage of non-consented user and device data that are known to facilitate workarounds to the AppTrackingTransparency (ATT) framework. Kochava remains committed to helping marketers adhere to Apple’s privacy guidelines with privacy-first measurement strategies.
- SKAdNetwork (SKAN) 5 will see the addition of support for re-engagement attribution. Up until now, support has been limited to acquisition attribution only. Kochava is excited to add this capability to our SKAN support model.
- In iOS 17, Apple will expand Private Relay by allowing app developers to create and enforce their own private relay implementation within their apps. Currently, Private Relay is an opt-in available for iCloud+ subscribers only.
- Vision Pro promises to ignite new interest and viability in AR and metaverse applications. Kochava will provide out-of-the-box measurement support of apps on Vision Pro via our iOS software development kit (SDK).
- Privacy Pillars are focused on a variety of new, privacy-related functionalities largely centered around reading resources and user behaviors across the OS. Of particular note, Enhanced Private Browsing for Safari will completely block known trackers from loading on pages, and remove tracking added to any URLs as users browse.
If you have more time to explore and learn, read on as we unpack each of these points in greater detail.
SKAN 5
With much of the industry still running on SKAN 2-3, and SKAN 4 adoption just beginning to trickle in, it had been thought that Apple might not introduce any SKAN updates at this year’s WWDC. In fact, the SKAN callout was so subtle that it could’ve been easily missed. As it turns out, Apple wanted to re-engage (pun intended) on the topic by adding re-engagement support into SKAN. More details on how this works will be forthcoming, but the ability to attribute ad taps that lead existing users back into the app is a welcome addition. That being said, re-engagement targeting is already a challenge on iOS, given the low rates of IDFA availability. Will Apple copy Google’s playbook for Android Privacy Sandbox and introduce Topics or Private Audience -esque capabilities?
Either way, it remains to be seen how fast the industry can adopt all of the SKAN 4 updates and then take the step up to be on v5 in order to benefit from re-engagement attribution.
Read all about Kochava support for SKAN 4.0 here, and check out Kochava SKAN solutions.
Privacy Manifests
The Privacy Manifest is a file for outlining the privacy practices of third-party code in an iOS app, in a single standard format. This should make it easier for users to understand how their data is being used, and to make more informed choices about the apps they download and use.
The ATT framework continues to be expanded and at first glance, Privacy Manifests appear to gate certain types of third-party SDK signals behind ATT opt-in. Essentially, app developers will now have the ability to declare 3rd party domains that fall into various data collection categories within their app’s manifest (see developer documentation). Network requests to those declared domains will be blocked when the device’s user has not opted-in to tracking via the ATT framework for that app.
Additionally, Apple will provision a signature for 3rd party SDKs to sign their package with, which in turn will allow Apple to ‘identify’ an SDK within an app and inform the developer that the SDK they are integrating does (or does not) match the expected signature of that SDK. While Apple is not calling this a ‘registry’, it’s essentially what they are describing — and is the first step in mimicking what Google has done with their Google Play SDK Index.
It’s still too early to know the precise scope and impact of Privacy Manifest updates; nonetheless, it appears to decouple the app developer’s behavior from that of the SDK provider. The extent of this and repercussions of non-compliance is unclear, but we’ll continue to keep an eye on the developments, so stay tuned and subscribe to our newsletter for future updates.
Private Relay
Apple’s Private Relay helps protect online browsing activity by preventing websites from seeing the user’s IP address, in turn preventing advertisers from tracking user browsing activity across multiple websites. Currently, Apple provides private relay as an option for iCloud+ subscribers, which is applied only to Safari traffic and does not extend into app-level (or SDK) encrypted network traffic.
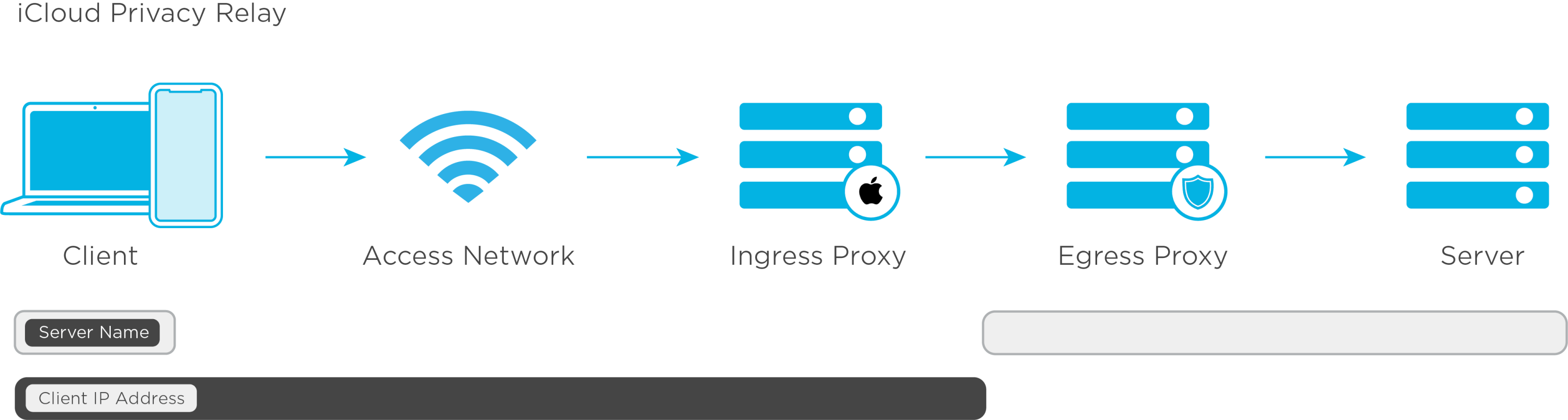
At WWDC 2023, Apple announced that app developers will be able to create and enforce their own Private Relay implementation within their app if they wish (view session video). This would allow apps to benefit from Private Relay regardless of whether the user has opted-in to the feature globally via iCloud+ and regardless of whether the global Private Relay applies to app network traffic.
If an app developer implements private relay within their app, IP addresses would be obfuscated for all network requests, including those coming from measurement partner SDKs. Needless to say, there would be a variety of implications to any functions that rely on IP address.
For now, this implementation relies on the app developer opting into this functionality. However, it is likely the first step in Apple eventually applying Private Relay to app-level network traffic automatically.
Vision Pro
Apple has entered the VR headset wars and Meta has certainly taken notice. It remains to be seen how Apple’s entrance into this space will act as a catalyst for AR and metaverse adoption among both consumers, developers, and AdTech players alike.
Bob Iger noted Disney+ will be available on Vision Pro from day 1. Other streaming services are sure to follow suit. With Kochava’s strength as the leader in measurement for media and entertainment apps, we’re excited to support our clients as they bridge entertaining experiences into this new realm and develop apps for Vision Pro.
Privacy Pillars
In the Privacy Pillars session, Apple introduced a number of new APIs designed to help app developers optimize their apps and services, while protecting user privacy. One example of this is the new Embedded Photos picker. This new API enables an app developer to allow users to share only specifically selected photos to the app, while not requiring the user to grant the app permissions to access their entire photo library.
Other new APIs included:
- Screen Capture picker
- Write-only calendar access
- Oblivious HTTP
- Communication Safety

EMBEDDED PHOTOS
PICKER

SCREEN CAPTURE
PICKER

WRITE-ONLY CALENDAR
ACCESS

OBLIVIOUS HTTP

COMMUNICATION SAFETY
While many of these announcements were not relevant to mobile or measurement in general (for example: restricting one app from reading data from another app on macOS), there were two more noteworthy call-outs:
Oblivious HTTP (OHTTP)
Related to Private Relay at the app level, which obfuscates the IP address of outgoing network requests from within a particular app – only if the app developer chooses to implement it.
Safari 17 – Stripping of Query String Parameters
As part of Safari’s expanded private browsing functionality, Apple says it will strip some query parameters from network requests while in private browsing mode.
For example, the id parameter of the url foo.com/?page=1&id=12345 might be removed by Apple, resulting in a url of: foo.com/?page=1
This does not impact mobile apps yet, but could prevent click and impression tracking from working while in private browsing mode — or any functionality which relies on identifiers within the URL query string rather than the body of the request.
Safari is often the first place we see changes that eventually make their way to the mobile app side, and this is one to watch as it would be the first time Apple makes an effort to reach into a network request and modify its contents, rather than simply blocking it.
Watch the related WWDC 2023 session here.
What’s next?
As the dust settles from the excitement of WWDC 2023, our team will be digging into the finer details in Apple’s documentation. Subscribe to our newsletter to receive ongoing updates and be sure to register for our upcoming webinar HERE where we will breakdown WWDC 2023 and take your questions.









